|
|
Progress Continues
We've already had 21401 updates since Dolphin 5.0. Keep up with Dolphin's continuing progress through the Dolphin Blog: August, September, and October 2023 Progress Report. |
|
|
The Dolphin Emulator Wiki needs your help! Dolphin can play thousands of games, and changes are happening all the time. Help us keep up! Join in and help us make this the best resource for Dolphin. |
NAND Usage Guide: Difference between revisions
No edit summary |
|||
| (15 intermediate revisions by 5 users not shown) | |||
| Line 2: | Line 2: | ||
== Dumping NAND with BootMii== | == Dumping NAND with BootMii== | ||
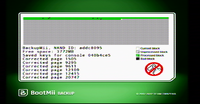
[[File:BootMii_Dumping.png|200px|thumb|right|BootMii Dumping]] | |||
To dump NAND with BootMii, you'll need: | To dump NAND with BootMii, you'll need: | ||
*A homebrewed console with BootMii installed | *A homebrewed console with [https://bootmii.org/download/ BootMii] installed | ||
*A SD card | *A SD card | ||
Access BootMii through the '''Homebrew Channel'''. Use a GameCube Controller or the Power and Reset buttons to navigate through the BootMii menus, as detailed [ | Access BootMii through the '''Homebrew Channel'''. Use a GameCube Controller or the Power and Reset buttons to navigate through the BootMii menus, as detailed [https://bootmii.org/faq/ here]. Select '''Options''' (gears icon) on the far right. Select '''Backup NAND''' (Green arrow from chip to the SD card), and wait until it completes. Once completed, remove the SD card and put it into your system. You should see a file named '''nand.bin''' on the SD Card. If you do, your NAND has been backed up. | ||
== Extracting NAND files == | == Automatic Import with Dolphin 5.0-3416 or newer == | ||
Select Tools > Import BootMii NAND Backup. Dolphin will decrypt and unpack the NAND. Device credentials and system files required for network services emulation will also be extracted automatically. | |||
== Manual Import == | |||
=== Extracting NAND files on Linux === | |||
# '''Extract''' the AES IV from keys.bin: <code>dd if=keys.bin of=aes-iv bs=1 skip=360 count=16</code> | |||
# '''Extract''' the per-console NAND key from keys.bin: <code>dd if=keys.bin of=nand-key bs=1 skip=376 count=16</code> | |||
# '''Decrypt''' the NAND image: <code>openssl enc -d -aes-128-cbc -in nand.bin -out nand-decrypted.bin -K $(hexdump -v -e '/1 "%02X"' < nand-key) -iv $(hexdump -v -e '/1 "%02X"' < aes-iv) -nopad</code> | |||
# '''Unpack''' the decrypted NAND image using zestig. The zestig source code can be downloaded [http://git.infradead.org/?p=users/segher/wii.git from here]. | |||
=== Extracting NAND files on Windows === | |||
Use [http://forums.dolphin-emu.org/attachment.php?aid=1383 NAND Tools] consisting of the followings to extract the files from '''nand.bin''': | Use [http://forums.dolphin-emu.org/attachment.php?aid=1383 NAND Tools] consisting of the followings to extract the files from '''nand.bin''': | ||
*cmd.lnk | *cmd.lnk | ||
| Line 17: | Line 28: | ||
Place '''nand.bin''' and '''keys.bin''' you've acquired from the last section into the working directory, then open '''cmd.lnk''' (A shortcut file that will open <var>%windir%\system32\cmd.exe</var> into shortcut's current directory) then do the required steps: | Place '''nand.bin''' and '''keys.bin''' you've acquired from the last section into the working directory, then open '''cmd.lnk''' (A shortcut file that will open <var>%windir%\system32\cmd.exe</var> into shortcut's current directory) then do the required steps: | ||
{| class="wikitable" | {| class="wikitable" | ||
|- | |- | ||
| Line 40: | Line 52: | ||
| It will close command prompt. | | It will close command prompt. | ||
|} | |} | ||
The new folder <var>\nand\</var> will be created in the working directory | The new folder <var>\nand\</var> will be created in the working directory. | ||
== | === Placing the NAND files into Dolphin === | ||
# Dolphin versions before {{revision|5.0-4416}} can't take the original '''SYSCONF''' file from real consoles, it has its own specially made SYSCONF file in <var>\Wii\shared2\sys\</var>. Use it to overwrite on top of the original SYSCONF file in <var>\nand\shared2\sys\</var> (under NAND tools' working directory). | |||
# Finally, place everything from <var>\nand\</var> into the <var>\Wii\</var> subdirectory. | |||
[[Category:Tutorials]] | [[Category:Tutorials]] | ||
Revision as of 22:17, 14 June 2020
NAND Flash Memory is the built in memory of the Wii console. It houses save data, downloaded channels, and the Wii Menu. Some games may require files only found in a full NAND dump to work correctly. The easiest way to do that is with BootMii. For alternate methods, see the forum thread.
Dumping NAND with BootMii
To dump NAND with BootMii, you'll need:
- A homebrewed console with BootMii installed
- A SD card
Access BootMii through the Homebrew Channel. Use a GameCube Controller or the Power and Reset buttons to navigate through the BootMii menus, as detailed here. Select Options (gears icon) on the far right. Select Backup NAND (Green arrow from chip to the SD card), and wait until it completes. Once completed, remove the SD card and put it into your system. You should see a file named nand.bin on the SD Card. If you do, your NAND has been backed up.
Automatic Import with Dolphin 5.0-3416 or newer
Select Tools > Import BootMii NAND Backup. Dolphin will decrypt and unpack the NAND. Device credentials and system files required for network services emulation will also be extracted automatically.
Manual Import
Extracting NAND files on Linux
- Extract the AES IV from keys.bin:
dd if=keys.bin of=aes-iv bs=1 skip=360 count=16 - Extract the per-console NAND key from keys.bin:
dd if=keys.bin of=nand-key bs=1 skip=376 count=16 - Decrypt the NAND image:
openssl enc -d -aes-128-cbc -in nand.bin -out nand-decrypted.bin -K $(hexdump -v -e '/1 "%02X"' < nand-key) -iv $(hexdump -v -e '/1 "%02X"' < aes-iv) -nopad - Unpack the decrypted NAND image using zestig. The zestig source code can be downloaded from here.
Extracting NAND files on Windows
Use NAND Tools consisting of the followings to extract the files from nand.bin:
- cmd.lnk
- nand-aes-dump.c
- nand-aes-dump.exe
- NAND-bin2raw.exe
- zestig.exe
Place nand.bin and keys.bin you've acquired from the last section into the working directory, then open cmd.lnk (A shortcut file that will open %windir%\system32\cmd.exe into shortcut's current directory) then do the required steps:
| Step # | Code to enter | Explanation |
|---|---|---|
| 1 | nand-aes-dump.exe | It will extract your AES key from your nand.bin into a file called nand-key.bin. |
| 2 | NAND-bin2raw.exe nand.bin nand_dec.bin | It will start the decrypting process and you should now have 2 bin files: encrypted and decrypted nand dump.
|
| 3 | zestig.exe nand-key.bin nand_dec.bin nand | It will extract everything from nand_dec.bin and place them into a new folder called "nand". |
| 4 | exit | It will close command prompt. |
The new folder \nand\ will be created in the working directory.
Placing the NAND files into Dolphin
- Dolphin versions before 5.0-4416 can't take the original SYSCONF file from real consoles, it has its own specially made SYSCONF file in \Wii\shared2\sys\. Use it to overwrite on top of the original SYSCONF file in \nand\shared2\sys\ (under NAND tools' working directory).
- Finally, place everything from \nand\ into the \Wii\ subdirectory.